Network Switches
Our focus is to build a faster, secure, resilient network, reduce the complexity and allow your network to have automated moves, adds and changes. We focus on simplification, multitenancy and network segmentation at scale. Harmonix Technologies designs solutions to meet your data center, core or edge.
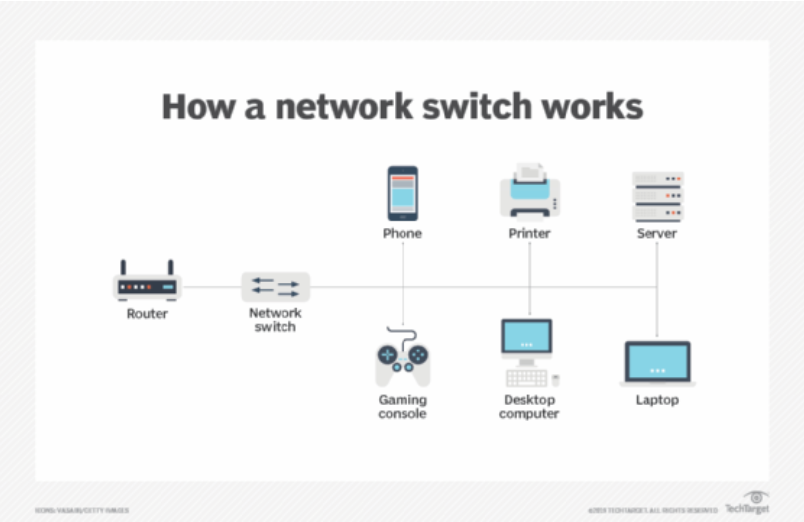
What is Data Switching
Switches, physical and virtual, comprise the vast majority of network devices in modern data networks. They provide the wired connections to desktop computers, wireless access points, industrial machinery and some internet of things (IoT) devices such as card entry systems. They interconnect the computers that host virtual machines (VMs) in data centers, as well as the dedicated physical servers, and much of the storage infrastructure. They carry vast amounts of traffic in telecommunications provider networks.
A network switch can be deployed in the following ways:
- Edge, or access switches: These switches manage traffic either coming into or exiting the network. Devices like computers and access points connect to edge switches.
- Aggregation, or distribution switches: These switches are placed within an optional middle layer. Edge switches connect into these and they can send traffic from switch to switch or send it up to core switches.
- Core switches: These network switches comprise the backbone of the network, connecting either aggregation or edge switches, connecting user or device edge networks to data center networks and, typically, connecting enterprise LANs to the routers that connect them to the internet.
Network device layers
Network devices can be separated by the layer they operate on, defined by the OSI model. The OSI model conceptualizes networks separating protocols by layers. Control is typically passed from one layer to the next. Some layers include:
- Layer 1- or the physical layer or below, which can transfer data but cannot manage the traffic coming through it. An example would be Ethernet hubs or cables.
- Layer 2- or the data link layer, which uses hardware addresses to receive and forward data. A network switch is an example of what type of device is on layer 2.
- Layer 3- or the network layer, which performs similar functions to a router and also supports multiple kinds of physical networks on different ports. Examples include routers or layer 3 switches.
With Virtual Private Network (VPN) you can extend your network safely.
Many options are available, allowing the network to be expandable for growth that suit every budget. With Licensing, Maintenance and Service options being customizable and affordable.
Flexibility means agility. True power in networking comes from the ability for the infrastructure to diversify, to be nimble and capable of support the infrastructure in its totality.
The ability for your network to be capable of producing exactly what your infrastructure needs is crucial. Never compromising the quality, when designing, this is an essential component. The maximization of your resources is important for efficiency.
Multi Service/Layer 3 Networking Solutions
Until recently, business was conducted via separate networks for voice, video, surveillance and data. Of these the Data network has now become the most important component in Communications. It is a reality that more information is now being sent as IP traffic than any other form. As a result vast amounts of additional investment are continually being pumped into the development and improvement of data networks. At Harmonix, we specialize in the design and implementation of Layer 3 Networks. We build a strong network foundation with VLAN and tagging to support voice, video, and data transport on a single layer 3 Multiservice Network. In addition, we highly recommend data infrastructure elements that support power over Ethernet. The POE Element is critical to Multiservice Networking as it allows Phones, IP Cameras, Wireless APs and other devices to receive power over the data network rather than from the 110V Outlet.
Layer 3 Networking is about bringing together a range of communications media into a single coherent core network infrastructure. It’s about carrying multimedia traffic, in real time, to wherever you want it on the network. Layer 3 networking technology now allows the integration of the following types of traffic onto your Local or Wide Area Network, creating, amongst other things, voice, video and data applications to the desktop and a unified messaging infrastructure.
Importance of MultiService/Layer 3 Networks
Think about what makes a modern enterprise successful. In today’s Information Society success or failure is increasingly determined by an organization’s ability to obtain and process information and communication. The ease and speed at which information is transferred between your enterprise and its clients or partners has become a key component to productivity and customer satisfaction. It is now a key competitive differentiator. The number of mediums utilized for this communication has been increasing dramatically over the last few years. Customers and end-users want to be able to communicate utilizing various types of voice, video and data services. Enterprises must move to make themselves accessible to end users and customers across many different communication platforms if they are to survive in the future. The Multiservice/Layer 3 Network brings the mediums of voice, video and data together under one network allowing for new applications to evolve utilizing these mediums to gain a competitive advantage.
Emerging Multi Service Network Architecture
Multiservice network architecture combines the multiple layers of legacy architecture into fewer network elements, thereby removing barriers to operational efficiency and flexibility. Convergence creates a unified network that operates cohesively to promote efficiency, enhance service features, and offer cost savings—key elements of today’s competitive marketplace. Emerging network technologies will soon render today’s complex mix of network elements obsolete and will help network operators run simpler and more flexible networks. The array of equipment required to string together time-division multiplex (TDM), asynchronous transfer mode (ATM), and frame-based packet-switching functions has become increasingly complicated and inefficient. Network service providers must run separate operations for multiple network overlays. This requires expertise in multiple technologies with equipment from multiple vendors to manage each transport-network type. In addition to the expense of supporting this infrastructure, the length of time required to provision services from such a platform reduces network-operator competitiveness.
The new paradigm for building or expanding the network infrastructure, on the other hand, converges the functions of time-division backbone switches into fewer network elements. The result is an infrastructure that is simpler, less expensive to manage, and capable of delivering more sophisticated and flexible functions. These newer architectures remove barriers to operational efficiency and flexible provisioning by creating a unified network that can be operated and managed cohesively. Converged architectures combine the functions of multiple layers of the open systems interconnection (OSI) network model into fewer pieces of equipment. This dramatically simplifies network topology and reduces capital investments and the cost of operations. In addition, this design significantly enriches service features because of the intelligent capabilities within the consolidated device.
Next-Generation Multi Service Networks
Traditional multiservice networks focus on Layer 2 Frame Relay and ATM services, using a common ATM backbone to consolidate traffic. This generation of ATM switches was easily extended to support DSL and cable broadband build-outs.
In contrast, next-generation multiservice networks provide carrier-grade, Layer 3 awareness, such as IP and MPLS, in addition to traditional Layer 2 services. These next-generation multiservice networks can take the form of ATM-, blended IP+ATM-, IP/MPLS-, or SONET/SDH-based networks in order to deliver multiple traffic services over the same physical infrastructure.
Even with the existence of next-generation technology architectures, most providers are not in a position to turn over their core technology in wholesale fashion. Provider technology is often on up-to-decade-long depreciation schedules, and functional life must often parallel this horizon, even if equipment is repurposed and repositioned in the network. Then there is the customer-facing issue of technology service support and migration. Though you might wish to sunset a particular technology, the customer is not often in support of your timetable. This requires a measured technology migration supporting both heritage services along with the latest service features. Next-generation technology versions are often the result, to allow new networking innovations to overlap established network architectures.
Layer 3 In Depth
Internet Protocol Virtual Private Network (IP VPN) is a group of technologies that are widely used by corporations and service providers to provide secured, private and scalable communications with proper QoS, over a public IP based infrastructure such as the Internet and Service Provider shared IP networks. IP VPN is replacing the traditional VPN technologies such as ATM VPN, Frame Relay VPN and TDM based VPN to become the main stream of the VPN services, though interfaces to the existing technologies exist in some cases.
The core technology of VPN is the encapsulation or tunneling algorithms. Primarily, there are three types of IP VPN technologies: IP sec based IP VPN, MPLS based IP VPN and SSL base IP VPN. Different technologies may have different focus of benefits and serve different business purposes. The following are summaries of the three types of technologies, their main applications and limitations:
MPLS-based Layer 3 VPNs uses MPLS labeling algorithms and signaling protocols to encapsulate IP packets and distribute VPN-related information. MPLS based IP VPN can seamlessly interface with traditional VPN technologies such as ATM, Frame Relay and TDM etc. It can be an alternative or a complementary VPN solution to the legacy deployment. A primary advantage of MPLS is that it provides the scalability to support both small and very large-scale VPN deployments. It can support end-to-end QoS, rapid fault correction of link and node failure, bandwidth protection, and a foundation for deploying additional value-added services. MPLS technology also simplifies configuration, management, and provisioning, helping service providers to deliver highly scalable, differentiated, end-to-end IP based services. The service provider can offer SLAs by enabling MPLS traffic engineering and fast reroute capabilities in the core network. MPLS based IP VNP is a network based VPN technology for site-to-site VPN communications only.
IPSec protocol provides the framework for CPE-based Layer 3 VPNs. IPSec supports 1)Data confidentiality by encrypting packets before transmission; 2)Data integrity through authenticating packets 3)Data origin authentication; 4) Anti-replay; 5) Encapsulating Security Payload (ESP), for confidentiality. IPSec parameters are communicated and negotiated between network devices in accordance with the Internet Key Exchange (IKE) protocol. The IPSec protocol provides protection for IP packets by allowing network designers to specify the traffic that needs protection, define how that traffic is to be protected, and control who can receive the traffic. IPSec VPNs is a replacement technology to the traditional VPNs such as leased-line, Frame Relay, or ATM. The advantage of IPSec is that it meets network requirements more cost effectively and with greater flexibility by using the public IP network such as the Internet and service providers IP-based networks. IPSec is suitable for both site-to-site and remote-access VPNs.
Secure Sockets Layer (SSL) is for remote-access VPNs, instead of site-to-site VPNs. In the SSL based VPN, the Secure Sockets Layer protocol is used for packet encapsulation and user authentication. SSL provides access to Web-based applications from any location with a Web browser, an Internet connection, and without special client software. It provides secure connectivity by authenticating the communicating parties and encrypting the traffic that flows between them. SSL-based VPNs only support applications coded for SSL, including standard e-mail clients, Telnet, FTP, IP telephony, multicast applications, and applications requiring QoS.
Switches Partners


